Intelligent ZK Bridges
This blog presesnts you to understand how easy and better it is to build your cutting edge interoperable solution like a zk bridge on top of nil; Foundation. Before we start with the actual magic, there will be prerequisites like introduction to blockchain, ZKPs, bridges etc. so feel free to skip them to the concept of discussion stated in the table of contents as Understanding =nil; Foundation's DROP DATABASE *, zkLLVM, Proof Market. By the end of the blog you will understand how feasible nil; Foundation's technology is, for building your zk bridge.
Blockchain
Blockchain technology has ushered in a new era of trust and transparency in the realm of digital transactions. Leveraging decentralized networks, blockchains facilitate secure and transparent record-keeping through a chain of interconnected blocks, each containing a record of transactions. This distributed ledger system has become the cornerstone of cryptocurrencies, and distributed data, ensuring the immutability and integrity of transactions.
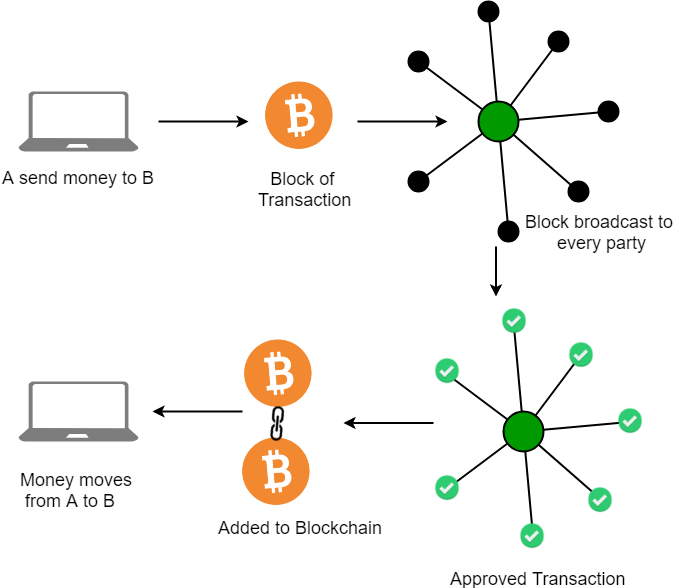
While the transparency of blockchain is a compelling feature, it also presents challenges, particularly in the realm of privacy. Traditional blockchains expose all transaction details to network participants. This transparency, while fostering trust, can become a hindrance when dealing with sensitive transactions or confidential business information.
In response to these privacy concerns, Zero-Knowledge Proofs (ZKPs) have emerged as a groundbreaking solution. But what is this ZKP even?
Zero- Knowledge Proofs
A zero-knowledge proof is like a secure magic trick in the world of cryptography. Imagine you want to convince someone that you know a special secret, but you don't want to spill the beans. In this magical process, there's a performer (the prover), an audience member (the verifier), and a challenge. The cool part is, that the performer can prove they know something without giving away any specifics—sort of like sharing a magical glimpse without revealing the actual enchantment. It's a way for individuals to publicly show they have certain knowledge or ownership without disclosing the nitty-gritty details. This cryptographic magic show involves proving the validity of a statement without unveiling anything more than the statement's validity itself.

Let's take an example to understand in simpler terms:
We are all familiar with concepts such as straight lines right from high school. Using that we will understand what Zero Knowledge proofs mean! Let's get started.
Let's say I have endpoints to a line (x1,y1) and (x2, y2) and I know that this line exists between these 2 points. Now I need to prove to you that I know this line exists with certain endpoints but I don't want to tell you the endpoints. Would you believe me if I say so that I know the line exists but I won't let you know the endpoints? No right! Because I might be bluffing. Now since I need you to trust me that I know and that I can't give you the actual coordinates, I will be using Zero Knowledge proofs to validate myself. So what I would do is, I would tell you points (x3, y3) and (x4,y4) which are a part of the line, they might be any 2 given points on the line and as we all know with 2 points given we construct a line and hence now you have the line I told you about without me revealing to you the actual endpoint coordinates. Hence "ZERO" knowledge was exchanged. You still don't know what the endpoints are or you have no knowledge of the endpoints of the line except the fact that I know that this line exists and that I know the endpoints.
Now in the above example, there are 2 parties, you and I. While I am the prover and you are the verifier. I prove to you that I know the line exists and you verified it.
There are a few properties to Zero Knowledge Proofs:
Completeness: A correct statement will be accepted by the verifier.
Soundness: An incorrect statement will be rejected by the verifier.
Zero-knowledge: The verifier learns nothing about the actual information being proved except the fact that the prover knows it.
Let's get a bit more tech-savvy and understand where in tech can we even apply these as for sure you are not just going to deal with lines of high school.
To build anything involving ZKPs you will need to know 2 ways in which you design systems which include the communication pipeline between the prover and verifier.
Hence we can classify ZKPs into 2 different types:
Interactive Zero-Knowledge Proofs: The prover and verifier engage in a series of back-and-forth interactions to establish the proof.
Non-Interactive Zero-Knowledge Proofs: The proof is generated by the prover and can be verified by the verifier without further interaction.
The one in the above example is the Non-Interactive ZKP also called by one of the most common names: zk-SNARK (stands for Zero-Knowledge Succinct Non-Interactive Argument of Knowledge)
Now since we have a fair idea of what ZKPs are we can deep dive into the major aspect of blockchain that requires ZKPs. So you might have heard about bridging, interoperability etc right this jargon is trying to solve one problem:
A blockchain is like a ledger and contains immutable data right. Now since we have a lot of blockchains in the current scenario with users, assets, data etc on diverse chains we will be encountering a situation where we might want our application's data and asset transfers between chains for the sake of users or the sake of low computation fees etc. But blockchains can't talk to each other! Yes, all this cryptography but inherently they can't communicate.
Bridges and why we need them?
So that's where bridges come into the picture. The bridges act as relayers to send data between chains and they have contracts that will instantiate the transaction on your origin chain to complete in the destination chain. Let's say you want to send some assets from Ethereum to Polygon right, you can use a bridge to transfer your assets and you will have your assets in polygon. They are just smart contracts on both origin and destination chains with some off-chain relaying to write to both contracts with a set of protocol rules.
Now you might be thinking this is great my problem is solved I can use bridges and asset transfers take place. But wait a minute...
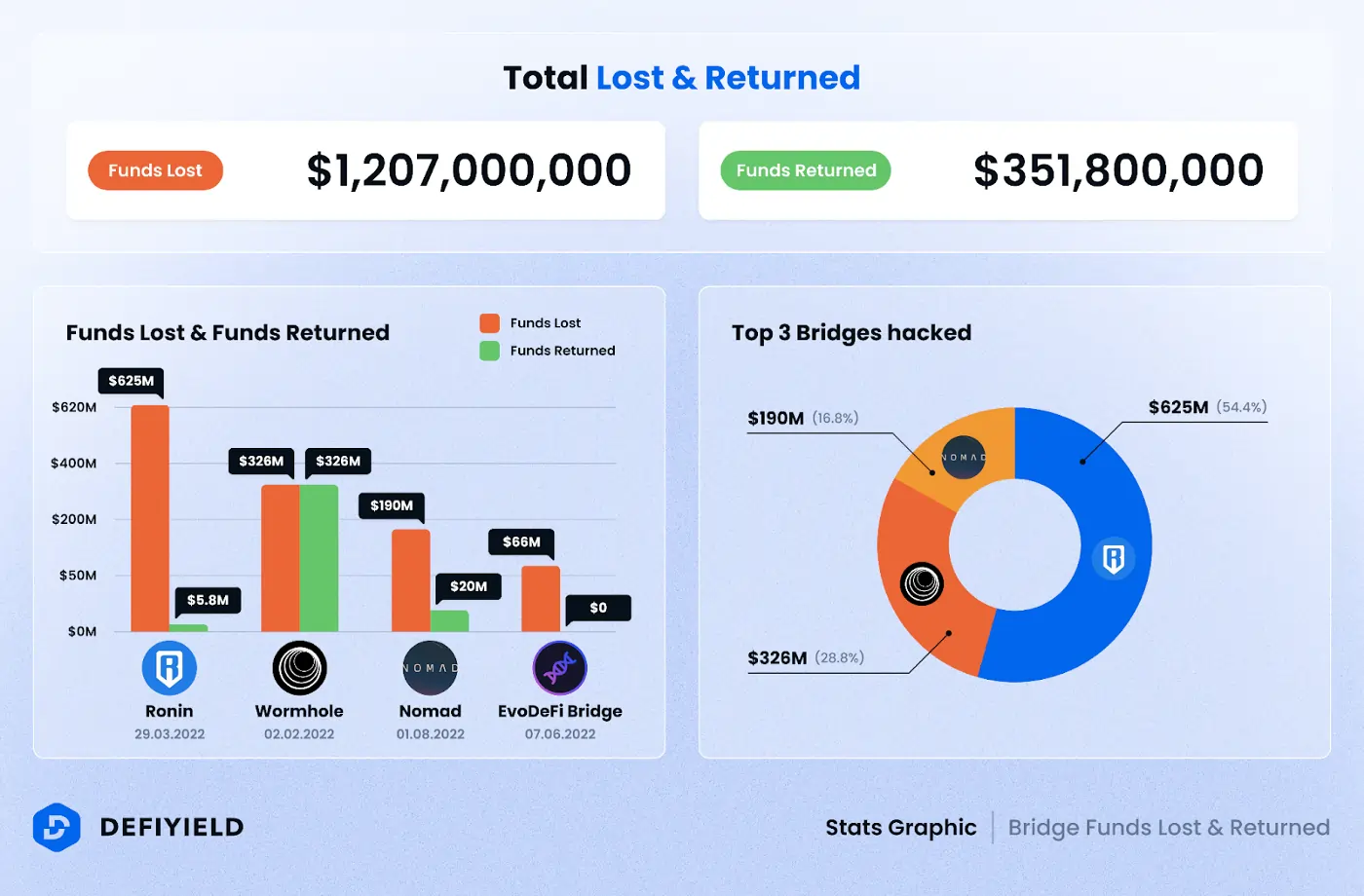
Now that is a lot of money to lose, right?
All that glitters is not gold my friend. Bridges seem to solve the billion-dollar solution to let blockchains talk to each other but also have become the major way to lose billions.
In the year 2022, losses totaling over $1.6 billion occurred due to exploits on these bridges. The interpretation of this figure can swing in two directions. On one hand, the substantial value moved through these bridges highlights a growing market demand for interoperability. On the flip side, it underscores a critical weakness in the broader blockchain ecosystem. The primary security concerns revolved around issues like bugs in the code, architectural blind spots (such as lacking fail-safes), and takeovers of committees or validators.
Now what is lacking in these bridges that are of conventional architecture where an origin chain contract receives data and an off-chain compute machine will call the destination chain contract and maybe also have a set of validators validating the transaction parameters to the destination chain?
Traditional bridges are often vulnerable to attacks because they rely on centralized operators and off-chain components. This makes them susceptible to data breaches, denial-of-service attacks, and man-in-the-middle attacks.
Traditional bridges often lack strong privacy guarantees. This means that user data can be exposed to third parties and used for malicious purposes.
Traditional bridges can be limited in terms of scalability. This can make them difficult to use for applications that require high throughput.
Traditional bridges can be vulnerable to exploits that allow attackers to steal funds.
Traditional bridges are often not transparent. This means that it can be difficult for users to understand how they work and to trust them with their assets.
In response to these challenges, developers are actively investigating alternative solutions, with a particular focus on cryptographic approaches. Leveraging the inherent properties of zk-SNARKs, these solutions aim to eliminate the necessity for the committee model, providing a path to scale the network more efficiently.
ZK Bridges: A More secure and Scaleable solution
Zero-knowledge (ZK) bridges have emerged as a promising remedy for the constraints associated with conventional bridges. ZK bridges harness the capabilities of zero-knowledge proofs, a cryptographic method enabling one party to demonstrate knowledge of specific information to another party without disclosing the actual details.
The incorporation of ZK proofs in bridges presents several benefits:
Enhanced Security:
- ZK bridges eliminate reliance on trusted third parties, thereby reducing the potential attack surface and minimizing security vulnerabilities.
Improved Scalability:
- ZK bridges exhibit enhanced scalability, enabling them to handle a larger transaction volume without compromising security, a notable advancement over traditional bridge mechanisms.
Stronger Privacy:
- User privacy is fortified by ZK bridges, ensuring that transaction data and asset balances remain confidential throughout the process.
This innovation not only addresses the limitations of existing bridge systems but also introduces a more secure, scalable, and privacy-conscious framework for cross-chain transactions.
Now that we have learned about what ZK bridges are let's have a quick look at how they work.
ZK bridges generally encompass the following key stages:
Deposit:
- Users initiate the process by securing their assets on the source blockchain. This action is accompanied by the creation of a zero-knowledge proof that encapsulates the details of the transaction.
Proof Verification:
- The generated zero-knowledge proof is transmitted to the destination blockchain, where it undergoes verification by a smart contract. This verification process ensures the authenticity and validity of the transaction.
Asset Issuance:
- Upon successful completion of the verification, the smart contract on the destination blockchain proceeds to issue the corresponding assets to the user, thereby completing the cross-chain transaction seamlessly.
Hence we can understand that we need data accessibility and the correct data accessibility in simple terms a ZK SNARK proof. And data management is something we have been doing since the early 1990s right? If we come forward from the time we started using DBMS, we might see that around 2010, blockchain was introduced for one of the reasons to evade the authority of data in centralized providers. Why? Simple because data can be mutated or altered.
So let's say we have Ethereum which is a blockchain and it has certain consensus rules and the data availability layer. Now let's take Solana, it has a different consensus and a different data availability layer.
So now, these data availability layers are going to give us the imagination that data accessing with different protocols is different. Secondly, the general procedure of bridging is: usually explicit data has to be provided from the first chain for the proof generation and is sent to the second chain. Post the verification only, the checking happens on the first chain whether the data is present. This means your bridge nodes have to be up and running all the time.
Secondly, you need to build your own ZK circuits which is again technically intensive process to handle as each of your use cases to use ZKPs will be different and hence will require different circuits.
Thirdly, once you have your ZK circuits for all your use cases, you will now have to need high computing power to run these circuits whenever a transaction occurs. Hence you will be prompted to pay a lot of fees if you start using service providers(AWS, Azure, which again makes your application centralized with a single point of failure).
Lets straightly, in short, note the problems ZK bridges face:
Data accessibility
Ability to implement ZK circuits
Compute to compile and run the ZK circuits
Understanding =nil; Foundation's DROP DATABASE *, zkLLVM , Proof Market
I do have something up my sleeve, that will help you build your ZK bridge technically in a simpler fashion and with less complexity than how traditionally ZK bridges are built. Apart from those 3 issues, I have also considered the fact that the time from learning to implementing or going zero to one in building your own ZK bridge is minimal.
Introducing you =nil; Foundation's three most important aspects for building ZK bridges, or migrating your already built ZK bridges, into a more efficient, secure and architecturally modular to implement:
DROP DATABASE *
zkLLVM
Proof Market

DROP DATABASE *
Imagine a single tool that can seamlessly manage multiple music players from different manufacturers, each with its unique interface and controls. This is the essence of =nil; DROP DATABASE *. Just as a universal remote control can operate various devices, =nil; DROP DATABASE * can transform into a fully functional node for different blockchain protocols. By implementing a replication protocol adapter for a specific protocol family, such as Bitcoin, Litecoin, Bitcoin Cash, and Feathercoin, =nil; DROP DATABASE * becomes a comprehensive node for each network.
But its capabilities extend beyond mere replication. =nil; DROP DATABASE * allows you to run multiple databases with their respective replication protocols within a single DBMS node. For instance, you could run Bitcoin, Ethereum, and Polkadot simultaneously, turning your DBMS instance into a fully functional node for each blockchain.
The beauty of =nil; DROP DATABASE * lies in its efficiency. You only need one powerful hardware setup to manage multiple databases and protocols, eliminating the need for dedicated nodes for each protocol. Moreover, =nil; DROP DATABASE * provides a consistent query language, state sharding, and data access capabilities for all supported databases. It's like using the same set of music player controls to manage different devices. In essence, =nil; DROP DATABASE * is a revolutionary tool that simplifies and streamlines the management of diverse blockchain protocols, offering a centralized solution for a decentralized world.
Solving the challenge of data accessibility is a significant stride forward, yet we're still faced with another hurdle – the ease of getting operations up and running seamlessly. Over the years, we've grown accustomed to interacting with databases through familiar query and write operations, whether they be SQL or NoSQL. Enter DROP DATABASE *, a solution designed to simplify the implementation of ZK bridges between blockchains and streamline interaction with nodes through straightforward query and write methods.
With DROP DATABASE, the transition from zero to one is remarkably smooth. The learning curve is minimal, as it leverages the familiarity we already have with traditional database queries. Imagine the power to implement intricate tasks without the need for an extra hour of learning something entirely new. This approach ensures that you can effortlessly integrate and work with DROP DATABASE – making complex operations as straightforward as your usual database interactions. Embrace a solution that not only addresses data accessibility but also prioritizes a user-friendly experience, allowing you to unlock the full potential of your endeavors without unnecessary complications.
zkLLVM
Picture yourself as a tech aficionado, immersed in the world of programming languages like C/C++ and Rust. Much like your passion for collecting CDs spans various genres and artists, navigating different CD players with their unique controls and interfaces can be a tedious task. Enter zkLLVM – the universal remote for blockchains.
In the realm of programming, zkLLVM functions as a compiler, translating high-level languages into circuits, akin to blueprints for constructing zero-knowledge proofs. Just as a universal remote simplifies the orchestration of CD playback, zkLLVM simplifies the creation of zero-knowledge proofs, enhancing accessibility and efficiency in the process.
Imagine zero-knowledge proofs as the secure tools for sharing music. They empower you to prove ownership of a specific CD without divulging its content, akin to demonstrating possession of a concert ticket without revealing the ticket itself.
zkLLVM takes this concept to the next level by automating the circuit generation process – think of it as a robotic assistant crafting blueprints on your behalf, saving you precious time and effort. This automation extends the reach of zero-knowledge proofs, making them more accessible to a broader spectrum of developers.
So, zkLLVM is not merely a compiler; it's a transformative force for blockchains, introducing seamless interoperability and heightened privacy. Just as a universal remote revolutionized how we engage with CD players, zkLLVM is set to redefine our interaction with blockchains, ushering in a new era of efficiency and innovation.
The Proof Market
Imagine you're craving a delicious yet complex dessert like a soufflé. Baking one requires precise measurements, perfect timing, and a bit of technical skill. You could attempt it yourself, but who wants to risk a deflated disaster? This is where the proof market comes in, your personal bakery for trustless treats.
Just like you order a soufflé in a bakery, the proof market lets you request specific "proofs," which are like verifiable guarantees on blockchain transactions. Think of them as elaborate, secure recipes that prove something happened without revealing all the ingredients (data).
Instead of baking yourself, you choose a "provider," a specialized chef in the proof market kitchen. These chefs compete on price and performance, ensuring you get the best soufflé (proof) at the best value. No need to trust any one chef blindly; the market incentivizes them to deliver perfect proofs every time.
Here's how it works:
Order your proof: Specify the type of proof you need, like proving a transaction is valid or someone is eligible for a reward.
The market bakes it: Specialized providers (chefs) compete to bake your proof (generate it) the fastest and most efficiently.
Quality check: The market verifies the proof to ensure it's delicious (accurate and secure).
Dessert time: If the proof is perfect, the provider gets paid, and you have your sweet reward – guaranteed trust in your blockchain transaction.
The proof market isn't just about satisfying your blockchain trust cravings. It's a versatile kitchen churning out secure and verifiable guarantees for a wide range of purposes. Here are just a few examples to whet your appetite:
1. Secure Cross-Chain Transactions:
Proofs can verify the validity of transactions on the source chain without revealing their details on the destination chain, preserving privacy and reducing trust assumptions.
This enables features like confidential cross-chain asset transfers, private cross-chain swaps, and anonymous voting on cross-chain governance proposals.
2. Scalable Cross-Chain Data Verification:
Proofs can guarantee the integrity and authenticity of data transferred across chains, without requiring full data replication on both sides.
This allows for lightweight cross-chain verification of identity, credentials, and other sensitive information, enabling efficient and trustless communication between different blockchain ecosystems.
3. Decentralized Cross-Chain Identity Management:
Proofs can provide verifiable claims about user identities and attributes without revealing private information.
This facilitates secure and trustless cross-chain authentication, empowering users to control their identities and interact with various dApps seamlessly.
4. Fraud-Proof Cross-Chain Marketplaces:
Proofs can verify the legitimacy of listings and transactions on cross-chain marketplaces, preventing fraud and boosting user trust.
This enables secure trading of assets, NFTs, and other digital goods across different chains, unlocking new possibilities for decentralized e-commerce.
5. Verifiable Off-Chain Computations:
Proofs can be used to validate the results of computation performed off-chain, while keeping the underlying data confidential.
This allows zk-bridges to leverage off-chain computation for complex tasks like privacy-preserving identity checks or fraud detection, while maintaining trust and transparency.
Implementing into your architecture
Drop Database Integration:
Unified Data Management: Drop Database serves as the centralized data management backbone for the ZK bridge, consolidating data from diverse blockchain networks.
Data Storage and Retrieval: Drop Database efficiently stores and retrieves data from various blockchain networks, enabling seamless asset transfers and data exchange.
Scalability and Performance: Drop Database's sharding capabilities, including data sharding and state sharding, to ensure scalability and performance to handle large volumes of transactions and data.
zkLLVM Integration:
Efficient ZKP Generation: zkLLVM's compiler capabilities streamline the generation of ZKPs, reducing computational overhead and improving transaction processing speed.
Privacy-Preserving Asset Transfers: zkLLVM enables privacy-preserving asset transfers by generating ZKPs that prove asset ownership without revealing asset details.
Enhanced Protocol Efficiency: zkLLVM's optimization contributes to the overall efficiency of the zk bridge, reducing transaction latency and improving throughput.
Proof Market Integration:
Decentralized ZKP Marketplace: The Proof Market provides a decentralized marketplace for buying and selling ZKPs, enabling bridge users to access the proofs they need for their transactions.
Transparent ZKP Procurement: The Proof Market's transparent nature ensures fair pricing and auditable transactions for ZKPs, fostering trust and security.
User-Friendly ZKP Access: The Proof Market integration facilitates seamless access to ZKPs for bridge users, enhancing the user experience.
Architectural Overview:
Data Layer: Drop Database resides at the data layer, providing unified data storage and management for the ZK bridge.
Proof Generation Layer: zkLLVM operates at the proof generation layer, efficiently generating ZKPs for privacy-preserving asset transfers.
Transaction Layer: The Proof Market is integrated into the transaction layer, facilitating the procurement of ZKPs for various transactions on the ZK bridge.
Data Flow:
Users initiate asset transfers or data exchange requests on the ZK bridge.
The zk bridge interacts with the Drop Database to retrieve relevant data from the connected blockchain networks.
Using zkLLVM compile your circuit.
The ZK bridge utilizes the Proof Market to generate proofs for verifiers if necessary, ensuring transparency and fair pricing.
The ZK bridge verifies the validity of ZKPs and completes the asset transfers or data exchange transactions.
Benefits:
Enhanced Privacy: The integration of Drop Database, zkLLVM, and Proof Market strengthens the privacy-preserving capabilities of the zk bridge.
Improved Security: zkLLVM-generated ZKPs and the Proof Market's decentralized nature enhance the overall security of the zk bridge.
Increased Efficiency: Drop Database's sharding, zkLLVM's optimization, and Proof Market accessibility contribute to the zk bridge's scalability and performance.
User-Friendly Experience: Seamless integration of these technologies provides a convenient and efficient experience for ZK Bridge users.
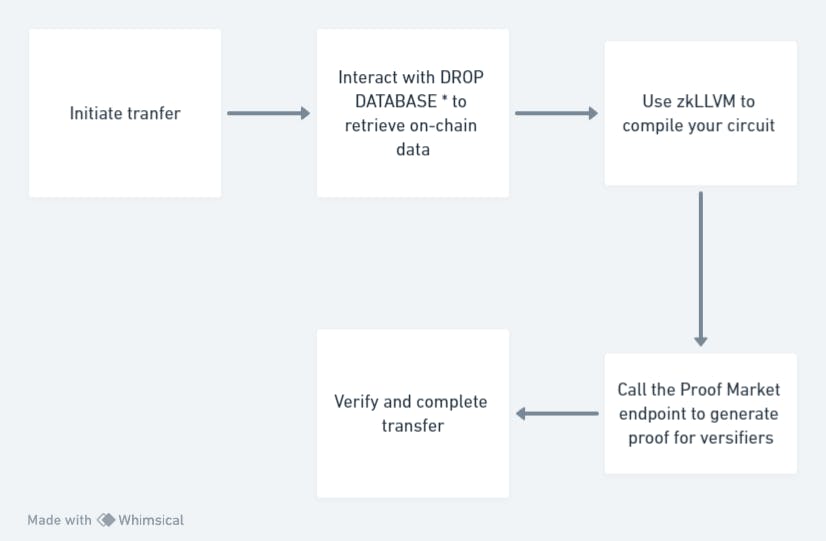
This architectural integration enables the zk bridge to leverage the strengths of Drop Database, zkLLVM, and Proof Market, resulting in a robust, secure, and efficient solution for blockchain interoperability.
Conclusion
The =nil; Foundation presents a revolutionary approach to blockchain interoperability for zk bridge technology, leveraging zkLLVM's efficient ZKP generation, Proof Market's decentralized ZKP procurement, and DROP DATABASE's seamless data management. This synergy enables robust, secure, and efficient asset transfers and data exchange which also is developer friendly, along with ease of implementation due to easy syntax like usual DBMS, across diverse blockchain networks, fostering a more interconnected and collaborative blockchain/ ecosystem for building your ZK bridge or migrating your ZK bridge. Welcome to the world of interoperability!
